Method and apparatus for a web-based application service model for security management PDF
Preview Method and apparatus for a web-based application service model for security management
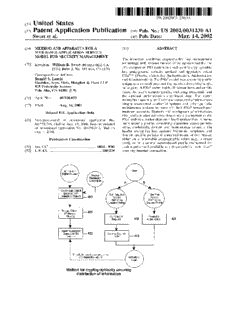
US 20020031230A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2002/0031230 A1 Sweet et al. (43) Pub. Date: Mar. 14, 2002 (54) METHOD AND APPARATUS FOR A (57) ABSTRACT WEB-BASED APPLICATION SERVICE MODEL FOR SECURITY MANAGEMENT The invention combines cryptographic key management (76) Inventors: William B. Sweet, Morgan Hill, CA technology With various authentication options and the use of a companion PKI system in a Web-centric cryptographic (US); John J. Yu, Milpitas, CA (US) key management security method and apparatus called Correspondence Address: PXa3TM (Precise eXtensible Authentication, Authorization Ronald S. Laurie and Administration). The PXa3 model uses a security pro?le Skadden, Arps, Slate, Meagher & Flom LLP unique to a network user and the member domain(s) he/she 525 University Avenue belongs to. A PXa3 server holds all private keys and certi? Palo Alto, CA 94301 (US) cates, the user’s security pro?le, including credentials and the optional authentication enrollment data. The server (21) Appl. No.: 09/930,029 maintains a security pro?le for each user, and administrators simply transmitted credential updates and other periodic (22) Filed: Aug. 14, 2001 maintenance updates to users via their PXa3 server-based Related U.S. Application Data member accounts. Domain and Workgroup administrators also3perform administrative chores via a connection to the (63) Non-provisional of provisional application No. PXa Web site, rather than on a local Workstation. A mem 60/225,796, ?led on Aug. 15, 2000. Non-provisional ber’s security pro?le, containing algorithm access permis of provisional application No. 60/239,019, ?led on sions, credentials, domain and maintenance values, a ?le Oct. 4, 2000. header encrypting key, optional biometric templates, and domain-speci?c policies is contained in one of tWo places: Publication Classi?cation either on a removable cryptographic token (e.g., a smart card), or on a central server-based pro?le maintained for (51) Int. Cl.7 ..................................................... .. H04L 9/00 each member and available as a doWnloadable “soft token” (52) U.S. Cl. .. ..... ..380/278 over any Internet connection. Information! Digital Content Access Permission Credenilats Create Data Object (ptaintext) with ' Embedded Objects _ 400 US$211?“ uzgéellgs Permission Permission Security Pro?le Security Pro?le V Encrypt Object _ (Embedded 405 Objects) Authenticate Automatic Request — 410 Authorization — 420 ‘ t Transmit Encrypted Object over the — 425 Transmit Security network Pro?le -——~ 415 Only Authorized Users can decrypt the transmitted object Authorized - User Method for cryptographicalty securing distribution of information Patent Application Publication Mar. 14, 2002 Sheet 1 0f 11 US 2002/0031230 A1 Random Value (Generated for each?le) (III-I..." '0 Q o 0 0 Maintenance Dom in Va" ‘e a ue Value _) COMBINER (Shared by ‘e (Updated by the everyone in the ‘ Domain Authority) Domain) " I ‘IIIIIIIII _ ‘e‘ ‘ n ‘ ‘ watt-a ge?” EncCrryepdteinotni/aDlesc-rbyapsteido n a‘ of the Random Value 0 0 Q I I I - : information about the ?le contents including its creator, the CKM® domain and f ‘ workgroup identity and maintenance level, creation date, encryption algorithm .* " information, digital signature. credential indicies, etc. .3 " Fi|e Header I RandomValue 101 o10.‘.1o01l‘ nnwa.jgbhlbn%78437*"1I48(9¢il§89pvBV9C“& I\/9®86TFGl°°/u"TA¢]B1IBN .,.."ud °°278[=]auY©FG1T‘fo&'\f0bvyfgs9fp|uBo¥K¥1rx©®eFv0tv‘6asjl;B9Tu46$|v;l(‘1[ Rmwmuqg?trez"‘hBliYejytjuuiwgromrmog115m..fnmmuvuunegiuu g'R/FMQO'AIO 1%o'?),,>n<,,>?>°1??,°11©=-¥Kueo O'IOO'FKIKYRTWEASYR'IAE Figure 1 Patent Application Publication Mar. 14, 2002 Sheet 2 0f 11 US 2002/0031230 A1 / (j=m2s mi _“0EE5555$d£32Q=.22:5525E2or..32222.Q35a66555.E6<2»802m5 2 ,23 a 1 ‘ ./llllllllll / \I\\\ \12: 5 L:L. Patent Application Publication Mar. 14, 2002 Sheet 3 0f 11 US 2002/0031230 A1 Pseudo Random Value 215 (Generated for ‘I I I I I I ' ' I each file) 0‘ o 0 '0 21 0 + 232 205 ‘. \ K o’ ‘o Maintenance Domain Value ‘‘ Value + (Shared by , (Updated by the everyone in the a Domain Authority) Domain) I I I 12° a“ ‘ ' ' - 120 a‘ w°rk'_"9 Key 230 Credentials-based c‘ (Umquel Encryption/Decryption : 235 200 of the Random Value n K . ' 0 I 0 : Information about the file contents including its creator, the CKM® domain and I I workgroup identity and maintenance level, creation date, encryption algorithm .‘ “ information, digital signature, credential indlcies, etc. ‘ CKM Header Random Value 101010...1 100 220a about the ?le contents including Is weator. the CKM‘ domain ard identity and maintenance leiel, mien date, encryption algorithm digital signature, uedennal IHIIUES‘ etc File Header Randmnvalue 101010 1001 domain and 220b DECENTRALlZED nigonthrr g PUBLIC NETWORK domain and 220C algorithm 1 domain and algorithm 220d Encrypted Data Object 330 Figure 3 Patent Application Publication Mar. 14, 2002 Sheet 4 0f 11 US 2002/0031230 A1 lnformation/ Digital Content Access Permission Credentials Create Date Object (plaimext) with 4 User Re uests User Has Embedded Objects _ 400 Acceqss Access Permission Permission Security Pro?le Security Pro?le Encrypt Object _ 405 (Embedded ' ' Objects) Authenticate Automatic l Request — 410 Authorization — 420 Transmit Encrypted + Object over the — 425 Transmit Security network Pro?le —-— 415 A 1 Only Authorized Users can decrypt I the transmitted object Authorized - - - - - - - - - - - - - - - - - - - - - - - - - - - User Method for cryptographically securing distribution of information Figure 4 Patent Application Publication Mar. 14, 2002 Sheet 5 of 11 US 2002/0031230 A1 Credential Categories: w Security Credentials— 501 This selection matrix is for all El - Trade Secret Directors in Engineering, IIIIIZIEIIEIHIZIIEZHIZIEIu E - Business Secret ——-> Marketing or Sales, who are I] - Proprietary authorized for Business Secret El - Con?dential information related to Project C w Functional Group Credentials-402 451E PD El - Engineering ——> El - Finance IZI - Marketing ——> E11 numb M 225 [I - Manufacturing E] - Legal E] - Sales ———> @zilali 0315a- 230 w Management Credentials~—503 El El - President’s Senior Staff E E - Directors |:| [j - Prod & Proj Managers Although all members with these [:1 E| ' Management Gradei credentials can read the file, only R w Geographical Credentials—504 Marketing Directors can write E] El - North America (modify) the ?le. [I E] ' Asia-Pacific |‘_'| [j - Europe R w Project Credentials-505 El El - ProjectA [I I] ' Project B |g| E - ProjectC -—_* Figure 5 Patent Application Publication Mar. 14, 2002 Sheet 6 0f 11 US 2002/0031230 A1 Receive Request for Access Permission __ 600 Credentials t Authenticate Request — 605 i Retrieve Security Pro?le (with Access —610 Permission Credentials Security Pro?le with Access Permission Credentials Information Transmit Security Generate Contained in Encrypted Pro?le Over the -_ 615 Cryptographic Object Network Working Key Transmit Working Key Over the -—- 620 Network Method for Providing Decryption Capabilities to Decentralized Public Network Users Figure 6 Patent Application Publication Mar. 14, 2002 Sheet 7 0f 11 US 2002/0031230 A1 System To Be Secured Select Portions of the System --~-- 700 i De?ne which Users will be Aliowed Access ——- 705 to Which Portions = Access Categories V Establish Access Codes for each —~ 710 Access Category i Assign Access Codes to Selected Portions — 715 of the System i Distribute Access Codes Over a Public —- 720 Network Securing a System Figure 7 Patent Application Publication Mar. 14, 2002 Sheet 8 0f 11 US 2002/0031230 A1 330 00 GDotueMoy H1annTevke t .YrrirrdS L r ._wlM-vdevAB A aO1. o_F_ll_. o M SMTlT Tilliet sVkr 3.mrmw._ m apmpt “SmKm5WTmS“ B Xe0_rnM M_us s mw=c_ mww anmekr i ‘uj ll3llit Htw o5rre e.e CBW mm Agln mE.l D NWsW3. ) 76" weu? ancs SdinCe 9 .“m 8 83m 14I| S"nO .2W“m K .;ym 9 Hm.) 1n. r_k._.ar. \ mmu, m k6 _ _ _ PXa3 Web Administration Architecture (Server-Side Detail) Figure 8 Patent Application Publication Mar. 14, 2002 Sheet 9 0f 11 US 2002/0031230 A1 FirewaillExternai Network -"'-'-'-1-'-'-“'-:-'-'-"-'-" Presentation Tier " Web Server '—801 __1025 7 ——————— —+ ———————— —— -—. | PXa3 Administrative Servlet/JSP : 305 | A r --------------- —"-1(',;0"“S"- ---- "I I Business Lo ic Tier @- ervice I g _ _ r940 = = Monitoring & —950 l i 935__ Domain Admin Server . Repomng i : Access Admlmstration l A A i v v {-930 s V Authentication ‘_945 i l Entity Member Access : l 936 _ Ema 8‘ T‘ike" Billing & I I ealls RStI'IGVHI : Auditing —955 : | D Database PXa3 Administration Service Figure 9
Description: